Securing access to your accounts and devices is crucial to protect yourself from hacking and unauthorized access to your data.
It’s okay to feel intimidated and overwhelmed by digital security recommendations, so we’re here to help. The tips below are intended to demystify the process. They can be done all at once or little by little. Every bit counts in making you more secure. You’d be surprised just how far simple measures like good password hygiene can go in keeping you safe.
If you need help implementing any of the guidance below or want to delve a little deeper, check out these fantastic interactive and user-friendly toolkits: Security Planner from Consumer Reports and Cybersecurity Toolkit for Journalists from the Global Cyber Alliance.
Use a password manager
If you take away one thing, let it be that using a password manager will make your life easier and your online accounts and data more secure. Today’s best practices for passwords (explained below) are to have long (think 16+ characters), complex (difficult to guess), and unique (one per account) passwords or passphrases. But creating and remembering a long, complex, and unique password for every account can feel like a Sisyphean task.
That’s where a password manager comes in. Password managers help generate randomized, complex passwords and keep them securely stored so that your brain doesn’t have to. Password manager mobile apps and web browser extensions streamline the whole process, filling in your usernames and passwords on websites it recognizes.
It’s entirely reasonable to have reservations about storing all your passwords in one place, and it’s important to understand that not all password managers are created equal. You should avoid storing your passwords on Google Chrome, Safari, or other browsers. Good password managers encrypt your passwords so that even if the company has a security breach, your passwords basically just appear as a nonsensical jumble of characters. Two password managers you may want to try are Dashlane and 1Password. Dashlane has a free version. 1Password costs money, but offers free accounts for journalists – here’s a review to help you decide.
Again, it’s normal to feel overwhelmed by updating your passwords and storing them securely, but each password you change helps keep you secure. Two approaches that work for people are either to block off an hour or two that you’ll dedicate to tackling your passwords, or, if this is too much, to make securing your passwords part of your everyday routine, starting with one password per day of your most sensitive account, like your email, and then moving on to your next account the following day. Here is a checklist we’ve compiled of the accounts you want to secure.
Compose strong, unique passwords
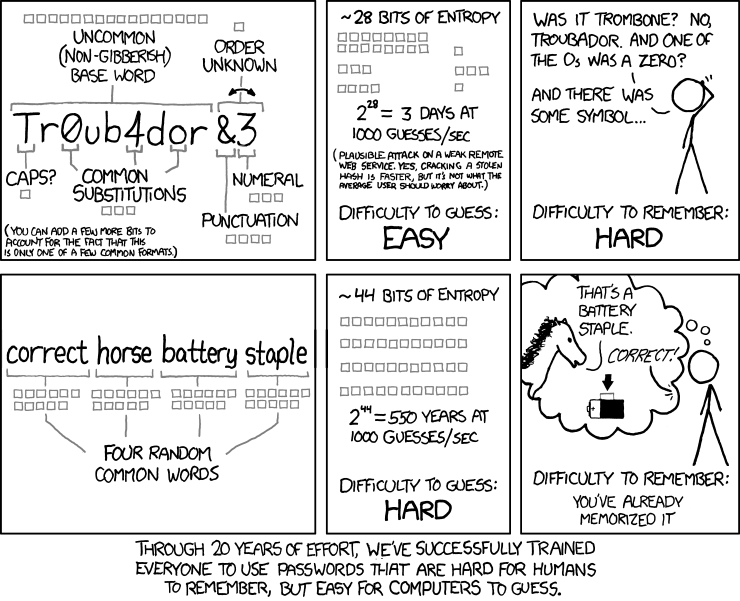
- We recommend your passwords to be at least 16 characters long. Longer is usually stronger when it comes to passwords, because cracking them through brute force requires more computing power and time for each character. You can also check to see how easily crackable your password is through sites like How Secure is My Password? (without entering your real password!) and Home Security Heroes. It can be tempting to use familiar names and places in your passwords or to swap out letters for correlative symbols, like “@” for “a” or “3” for “E.” Resist doing this. Instead, try using an automated password generator (like Secure Password Generator) or download a password manager (see below).
- Easy to remember but hard to guess. You don’t want others to be able to guess your passwords but you do need to be able to remember at least a couple of them, so consider using passphrases of five or more random words like “pursuit glitter sandy epic dances”. Avoid using song lyrics or common phrases as a passphrase. If you need help coming up with random words, you can try the dice method.
- One password per account. Data breaches that expose the usernames and passwords of online accounts by leaking these login credentials online have become commonplace. You can go to https://haveibeenpwned.com/, enter the email addresses you use, and check which of your accounts have been breached. If you’re reusing passwords across multiple accounts, if any one of those accounts was compromised in a breach, all of your other accounts with that same password and username are vulnerable as well. You will then need to immediately change the passwords on those accounts and never use those passwords elsewhere again. So use one password for each account you have. Remember that every little bit helps: start by making sure your most sensitive accounts (your email, finances, social media) have brand new, unique passwords and go from there.
It can be a lot to remember, so consider using a secure password manager (see below).
Activate multi-factor authentication whenever possible
Email, social media, and other sites that require a log-in usually offer the option of turning on multi-factor authentication (MFA). Sometimes also referred to as two-factor authentication or 2FA, multi-factor authentication is a security method that requires two distinct forms of identification to access a system or account. Those two forms are usually to provide something you know (your password) and something you have (a secondary device, code, or key).
There are different types of multi-factor authentication. These include:
- Using a code sent to your email or via SMS
- Using a code generated by a third-party authenticator mobile app or password manager
- Using a security key–a piece of hardware that you insert into your computer or phone or connect via bluetooth.
Of these three, SMS is the least secure option, but it’s still better than not using MFA. Writers, journalists, and activists at high risk of hacking, especially by a state actor, should use an authenticator app such as Authy or a security key such as a Yubikey.
(Bonus tip: if you use a Yubikey, you will want to have at least two, so you have a backup in case you lose the original.)
When you activate MFA, if someone tries to sign into your account, they won’t be able to complete authentication without access to your secondary device or key. Just like with passwords, you can take it one account at a time. Every bit helps. Here is a list of accounts to consider for setting up MFA along with links to instructions for how to set it up. You can check whether the application that you are using has multi-factor verification on https://2fa.directory/int.
Invent security question answers
Many sites require you to create a security question in the event that you forget your password. The questions tend to be simple and personal—meaning their answers could be easy for an attacker to dig up through a Google search.
Try to make your answers to these questions difficult, or pick a question and answer which isn’t Googleable. (For example, if the question is “Where were you born?” and a Google search of your name surfaces an article about the time you starred in your middle school play in Pleasantville, America, don’t pick that question or invent another answer.)
EFF recommends using a randomly-generated answer in response to these questions. Remember: your answer doesn’t have to be true, you just need to be able to remember it or to look it up! You can always save answers to security questions in your password manager if you’re worried you might forget them (see above).
Watch out for SIM hijacking
To protect from bad actors stealing your phone number, and with it access to authentication codes sent via SMS, you just need to take one simple step: call your cell phone provider and request to add a PIN to your account, which will then be required for any future changes. Store the PIN somewhere safe where you can access it when you need to remember it, like in your password manager. If you want more detailed information about SIM jacking–what it is, why bad actors do it, and how to protect yourself, check out Mozilla’s helpful guide.
Beware spam and phishing
Phishing (pronounced “fishing”) attacks are fraudulent emails, texts, DMs, calls, or websites created to manipulate people into sharing sensitive information like credit card numbers, bank account information, or login credentials – or into taking actions that unwittingly expose them or their organizations to cyberattacks. The people behind phishing attacks prey on natural emotions like our curiosity, desire to please, desire to help, etc. to get us to lower our guard and act quickly. Here are some examples of what phishing can look like.
Be careful when opening unexpected or unsolicited emails, and don’t open any unsolicited attachments or links without first verifying the sender. Look closely at the sender email address – not just the name it claims to be from. If you get an email with an attachment or link from a friend that you weren’t expecting, it is also good to send them a quick text and make sure it’s real. If you get an email telling you that you need to reset your password and you did not request this email, do not click on anything in the email. Instead, go to the website of the company or organization through your preferred search engine, log in, and address any password changes directly as needed. You can use this phishing quiz to test and improve your ability to recognize phishing attempts.
The guidance above was developed in consultation with cybersecurity experts at Freedom of the Press Foundation and PEN America.